Key
Management Service
Manage cryptographic keys and secrets with decentralized vaults and a comprehensive compliance management dashboard for security policies and regulations.
Manage cryptographic keys and secrets with decentralized vaults and a comprehensive compliance management dashboard for security policies and regulations.
Manage cryptographic keys and secrets with decentralized vaults and a comprehensive compliance management dashboard for security policies and regulations.
Traditional key management systems haven’t adapted to the realities and risks organizations with multi-cloud strategies face. Basic access controls, sparse metadata, and storage in one-size-fits-all key vaults should no longer be considered key management.You are not effectively managing your keys and secrets if you are not in control and aware of who creates and uses them. Knowing where your keys are stored can be an essential component for compliance with corporate security policies and/or regulations that differ by location and use case.
Entrust KeyControl is setting a new standard for key and secrets management by combining traditional key lifecycle management and a decentralized vault-based architecture with a comprehensive central policy and compliance management dashboard – the KeyControl Compliance Manager. The platform offers decentralized security with centralized visibility across the enterprise’s cryptographic assets. The powerful combination can help ensure data is protected in compliance with stringent regulatory requirements and keys and secrets can be geolocated and managed to respect data sovereignty mandates.
The KeyControl Compliance Manager offers a robust compliance dashboard for precise policy management and control of cryptographic keys and secrets enterprise-wide. This unified dashboard monitors assets in local or geographically distributed vaults.
Effective key control means managing risks efficiently. The integrated policy engine within the KeyControl Compliance Manager provides granular control, full visibility, traceability, compliance tracking, and an immutable audit trail for all keys and secrets.
This capability helps your organization stay aware and compliant with complex global data privacy, security, and sovereignty laws. You can tailor policies to your needs, distinguishing between test keys, production keys, or high-value keys, and ensure thorough metadata and documentation for each key created, surpassing the capabilities of traditional key management systems.
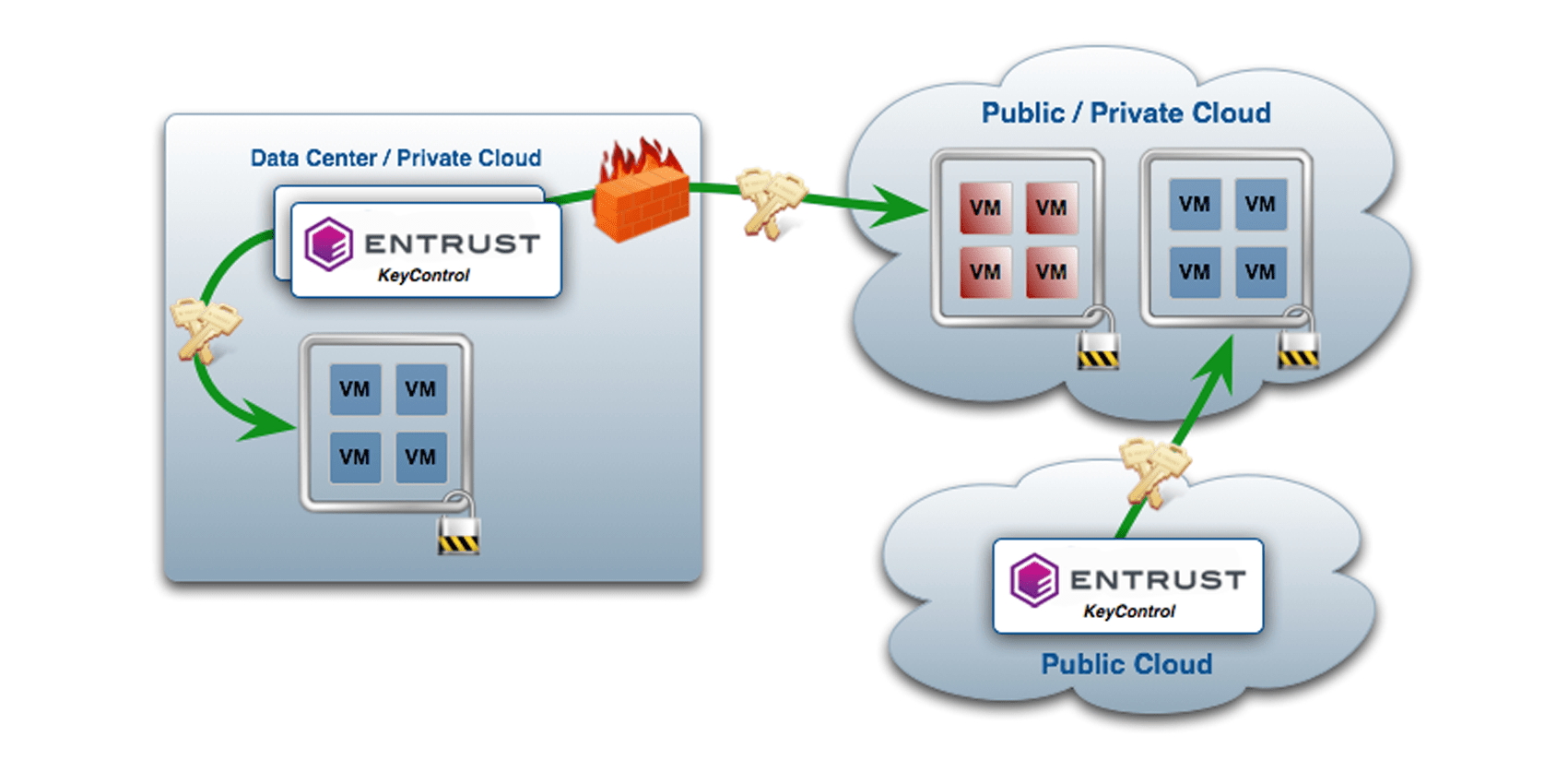
Many traditional monolithic key management solutions offer only a single, centralized repository for storing keys – which for some use cases can be like putting all your eggs in one basket.
The KeyControl platform offers a new distributed vault architecture supporting the creation of fully isolated vaults that can help your organization meet your compliance obligations related to geographical data residency and data sovereignty mandates for cryptographic assets, while reducing attack surfaces and providing flexible arrangements for disaster recovery (DR) and contingency planning.
Frequent data encryption key rotation is crucial. Managing workload encryption across different cloud platforms can be complex and error-prone. Our built-in key management policy simplifies this, ensuring consistency.
Entrust DataControl (formerly HyTrust) enhances multi-cloud workload security, streamlining protection across diverse cloud platforms. This boosts the security of your sensitive data and facilitates compliance with data privacy regulations.
Workloads go through many lifecycles, from staging to deployment to backup and eventual decommissioning. Each stage poses different risks of potential data theft or other misuse.
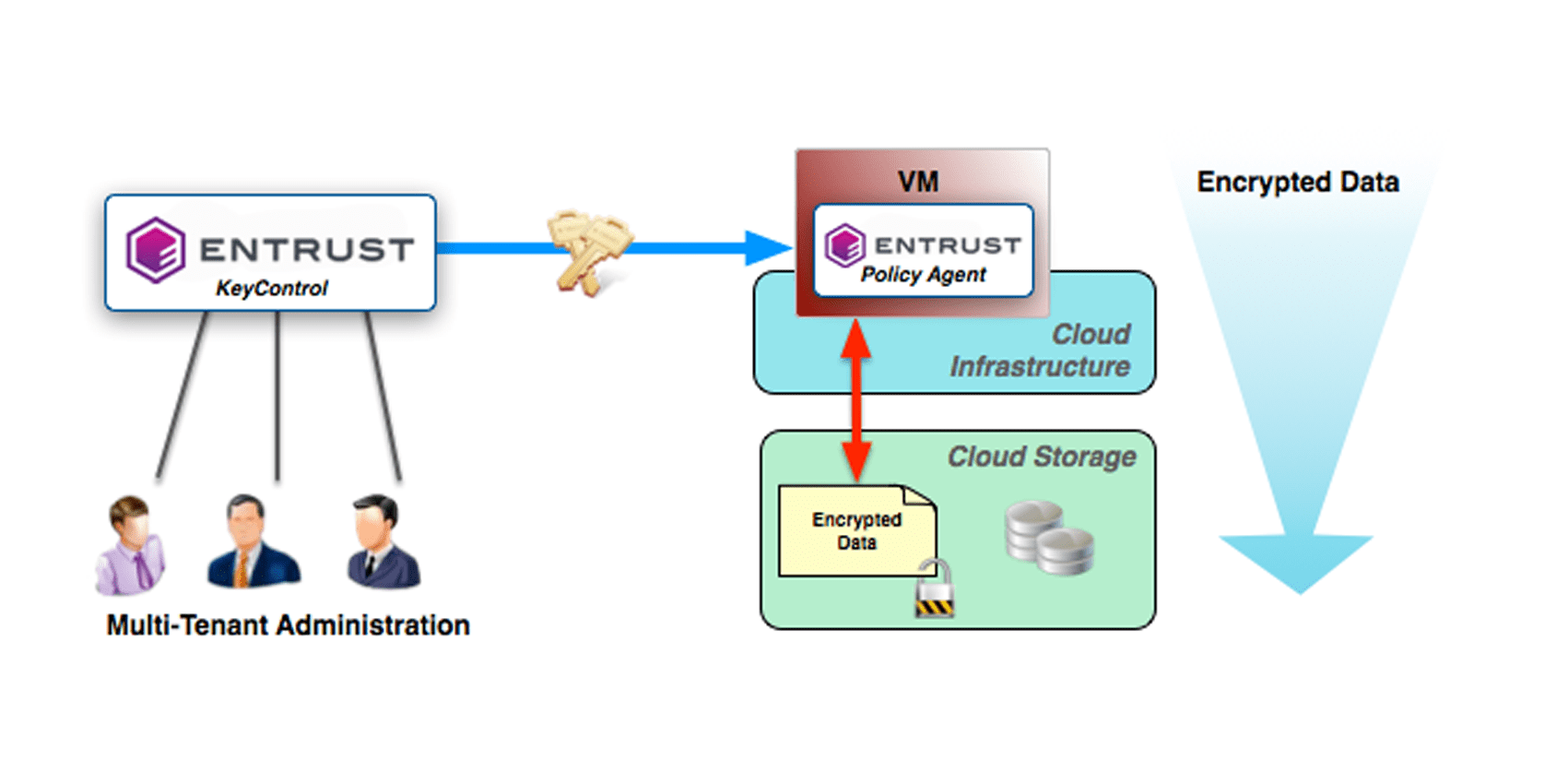
DataControl enables encrypted workload management across various infrastructures, including on-premises and top public cloud platforms. It offers a centralized and scalable solution for all your encryption keys, featuring the VMware-certified Key Management Server (KMS) KeyControl.
DataControl provides granular encryption for better security. The protection boundary does not stop at the hypervisor or at the data store; VMs are individually encrypted. Inside the VM, unique keys can be assigned to encrypt each partition, including the boot (OS) disk and swap partitions.
DataControl offers a single interface for seamless workload encryption, simplifying the process and delivering a superior user experience. It ensures zero downtime encryption and provides high-availability clustering for disaster recovery capabilities.
DataControl allows for robust policybased access controls to enforce separation of duties across different user personas. Prevent root users or system administrators from accessing sensitive data by enforcing access controls on encrypted volumes.
Previously, the concern existed that encryption and deduplication could not co-exist, given that encrypting data makes every block different. DataControl’s unique approach offers AES 256-bit encryption while maintaining 91% of storage deduplication benefit
Entrust CloudControl Comprehensive security for hybrid multi-cloud environments including centralized authentication, authorization, and audit control.
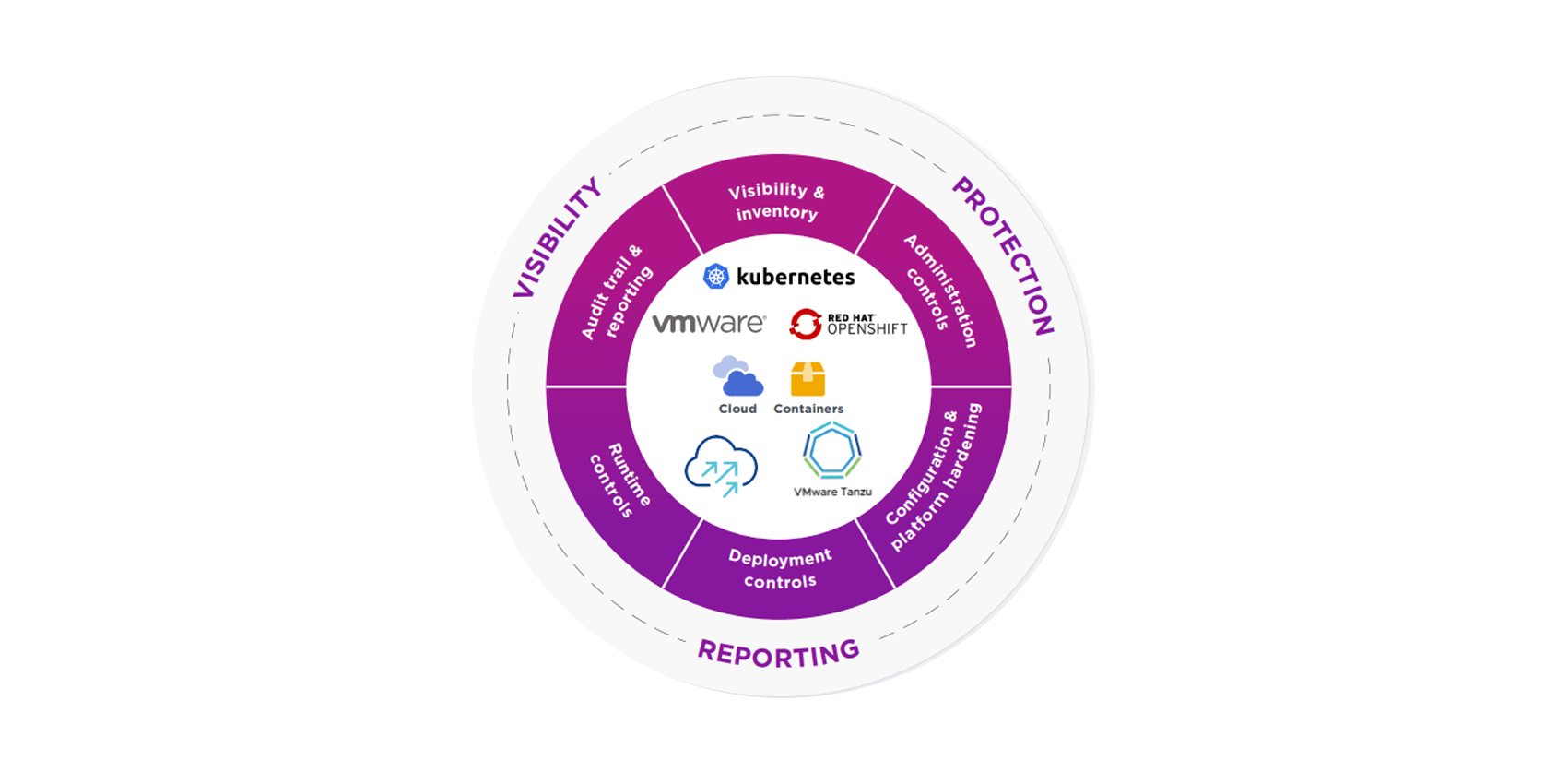
Reducing IT risks through a unified security framework As IT environments transition to hybrid cloud, security architectures must undergo a corresponding transformation. Entrust CloudControl (formerly HyTrust CloudControl) addresses the need for a comprehensive solution by providing a unified framework for security and compliance across the hybrid cloud – reducing both risk and operational overhead.
Comprehensive risk management CloudControl offers a wide range of capabilities that can be customized to meet any organization’s desired risk posture and control activity requirements. Supporting VMware Cloud Foundation, the centralized solution enables organizations to achieve authentication, authorization, and audit control for UI and API access to critical infrastructure resources in the ecosystem – including ESXi hosts, vCenters, NSX-T Managers, vSAN, and SDDC and associated workload and management domains
Gain full-stack multi-dimensional policies and industry-leading administration controls to protect against insider threats and human errors that cause downtime.
Acquire “create once, apply anywhere” policies that support consistent controls and eliminate manual efforts.
Eliminate multiple consoles and inconsistent security constructs, and gain security policies that support “security as code” automation.
Offers templates for compliance standards like CMMC, PCI DSS, NIST 800-53, HIPAA, FedRAMP, DISA STIGs, and more. Features include workload placement controls, logical segmentation, and comprehensive audit trail and reporting for control validation.
You gain insight with forensic quality logs for incident response root cause analysis and intent context.
Achieve authentication, authorization, and audit control (AAA) security for VMware Cloud Foundation (VCF). CloudControl provides role-based access controls (RBAC) for VCF that provides visibility into who is accessing resources in the VCF SDDC Manager and down to the ecosystem infrastructure components including ESXi hosts, vCenters, NSX-T Managers, and vSAN